Fundnet
From Mycomputer Notes
In thi chapters will introduced some terminology used by networking professionals and various types of computer networks. It also introduces an explanation on how standards ensure greater compatibility and interoperability among various types of computer netwroks. It also describes the OSI Model and the basic fonctions thtat takes place at each layer of the OSI Model.
Contents |
Networking Terminology
Data networks developed as a result of business applications that were written for microcomputers. The microcomputers were not connected so there was no efficient way to share data among them. It was not efficient or cost-effective for businesses to use floppy disks to share data.
Businesses needed a solution that would successfully address the following three problems:
- How to avoid duplication of equipment and resources
- How to communicate efficiently
- How to set up and manage a network
Networking Devices
- Networking devices
- Equipement that connect directly to a network segment. These devices are borken into two classifications.
End-User devices:
- Computers, Printers, Scanners and other deevices that provide services to the user. Devices that connect end-user to the network.
Network devices:
- All devices that connect the end-user devices together to allow them to communicate. Network devices are used to extend cable connections, concentrate connections, convert data formats and manage data transfers (i.e repeaters, hubs, switches and routers)
Repeaters:
- Layer 1 Devices on the OSI Referance Model.
- Regenerate adn retime network signals
- Single port "IN" & Single port "OUT"
Hub:
- Regenerate adn retime network signals
- Common connection point for device in the LAN
- Connects segments of a LAN
- Multiports (When a packet arrives at one port, it is copied to the other ports so that all the LAN segments
can see all the packets.)
- Also known as Multiport Repeaters
NIC:
- Layer 2 Devices because of the MAC Address (Media Access Control)
- Controls the Access of the host to the medium (the copper wire)
Bridges:
- Layer 2 devices
- Designed to create 2 or more LAN segments (seperate Collision Domains)
- Filter trafffic on the LAN (Filter frames)
- Keeps Track of which MAC addresses are on each side.
- Learned about devices by examinning MAC addresses.
- Maintain MAC Address Tables
- Broadcast
- Is a data packet that is sent to all nodes on a network.
- Broadcast Domain
- All the devices connected to a network that receives the data packet broadcast by a
node to all other nodes on the same network.
Bridges always foward broadcast because thy can not learn the broadcast MAC address of FF.FF.FF.FF.FF.FF; therefore all segments in a bridged environnement are considered to be in the same Broadcast Domain.
Swtiches:
- Another Layer 2 device
- Like Bridges they connect LAN segments
- Use a table of MAC addresses to determine the segment of which a frame needs to be transmitted and reduce traffic
- Foward and flood traffice based on MAC addresses.
- Each switch port is like its own Bridge
- Each host connect to the switch port has the full bandwith of the medium. This process is called microsegmentation.
- Microsegmentation
- the creation of private or dedicated segments -one host per segment. Each host does not have to compete for the medium banthwith with other host, so it has the full bandwith of the medium.
Routers:
- Internetworking device that passes data packets between networks based on Layer 3 addresses.
- Makes decisions regarding the best path for delivery of data on the network.
- Examing incoming packets.
- Choose the best path for the packets.
- Switches the packets to the proper outgoing network.
- Routers connect different Layer 2 technologies such as Ethernet, Token Ring & FDDI
Networking Topology
Network topology defines how computers, printers, network devices and other devices are connected. The topology describes the layout of the wire and devices as well as the paths used by data transmissions.
A topology can be both Physical and Logical.
- Physical Topology: physical layout of the wire media
- Logical Topology:how the host access the media to sent data
Common Physical Topologies:
- Bus Topology a.k.a linear topology
- Connects all the devices using a single backbone cable. This cable proceed from computer to the next like a bus line.
- The main cable segment must end with a terminator.
- The terminator absorbs the signal when the it reaches the end.
- Star and Extended Topologies
- Each host in the network is connected to the central device with its own cable.
Advantage Disadvantage
- When a cable has a problem only one host is affected.
- The rest of the Network remains operational.
- Central point is desirable for security or restricted acces.
- Cost more to implement.
- If the central device fails, the whole network fails.
- An extended star topology links individual stars together by connecting the hubs or switches.
- Ring Topology
- Host are connected in the form of a ring or cirlce.
- One host to the next and the last host to the first.
- This creates a physical ring of cable
- Hierarchical Topology
- Similar to an extended star. However, instead of linking the hubs or switches together, the system is linked to a computer that controls the traffic on the topology.
- Full Mesh
- Connects all devices (nodes) to each other for redudancy and fault tolerance. Usually implemented in WAN between routers.
Advantage Disadvantage
- Every node is physically connected to every other node creating redundant connection.
- Other.
- Other.
- For an small amount of nodes, the amount of media for the links and the number of the connections becomes overwhelming.
- Very expensive & difficult to implement.
- Parial Mesh
- At least one device maintains multiple connections to others with being fully meshed.
Partial mesh still provides redundancy by having several alternatives routes.
The logical topology of a network determines how the hosts communicate across the medium. The two most common types of logical topologies are broadcast and token passing.
- Broadcast (each host sends its data to all other host on the network medium, no order to follow, first come first serve)
- Token passing (electronic token is passed sequentially to each host. When that host can send data on the network. if the host has not data to sent on the network is passes the token to the next host)
Network Protocols
A Protocol is a formal set of rules and conventions that describes a particular aspects of how devices on a network communicate. Protocols determine the format, timing, sequencing and error control in data communication.
Protocols control all aspects of data communications:
- How the physical network is built.
- How the computers connect to the network.
- How the data is formatted for tranmission .
- How the data is sent.
- How to deal with errors.
These network rules are governed by different organizations & committees
- IEEE
- ANSI
- TIA
- EIA
- ITU
- CCITT
| LAN | WAN | MAN | SAN |
| LAN allow business to
locally shared computer files, printers efficiently and make internal communications possible. | WAN interconnects LAN.
WAN provide instant communications across large geographical areas to computer or file servers | A MAN usually consist of
two or more LAN in a common geographic area. A service provider is used to connect the LAN sites using private communication lines. | SAN is a dedicated high
performance network used to moved data between servers and storage
resources. |
| LAN Technologies:
|
WAN Technologies:
| SAN Offer the following features:
| |
|
LAN are designed to:
| WAN are designed to:
|
Bandwith
- Bandwith
- is defined as the amount of information that can flow through a network connection in a given period of time.
- Bandwith is finite - There are limits on the capacity of the network to carry information. Bandwith is limited both by the laws of physics and by the technologies employed to place information on the medium.
- Bandwith is not freee -Understanding banthwith and changes in the demand for it over a given period of time can save an individual or businesss a significant amount of money.
- Bandwith is a key factor in analyzing network performance, designing networks and understanding the Internet. A technician needs to understand bandwith and throughput on network performance and design.
- The demand for Bandwith is always increasing - As soon a a network has been updated with new technologies and new infrastructure to provide more bandwith, new application are creared to take advantage of the greater capacity.
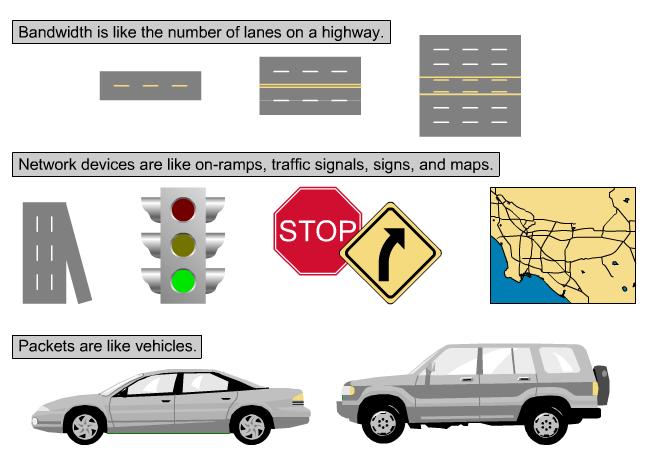
Bandwith Anologies
Networking Models
The concept of layers is used to describe communication from one computer to another. A conversation between two people provides a good opportunity to use a layered approach to analyze information flow. In a conversation, each person wishing to communicate begins by"
- Creating an idea. Then a decision is made on how to properly communicate the idea. For example, a person could decide to speak, sing or shout, and what language to use. Finally the idea is delivered. For example, the person creates the sound which carries the message.