Access Control List (ACLs)
From Mycomputer Notes
Routers provide basic traffic filtering capabilities, such as blocking Internet traffic, with access control lists (ACLs). An ACL is a sequential collection of permit or deny statements that apply to addresses or upper-layer protocols.
ACLs are lists of instructions you apply to a router's interface. These lists tell the router what kinds of packets to accept and what kinds of packets to deny. Acceptance and denial can be based on certain specifications;
- Source address
- Destination address
- Port number
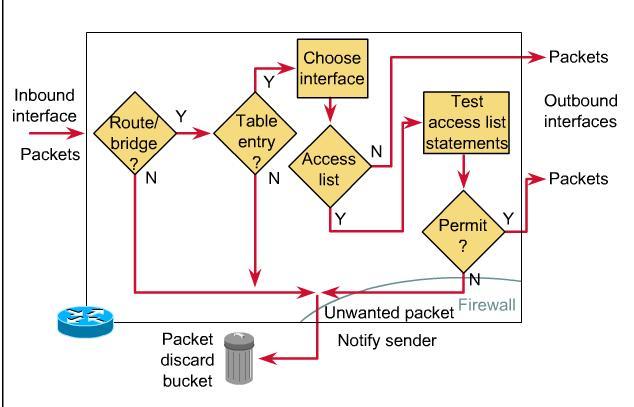
An ACL can be created for all Routed Protocols Routed Protocols to filter packets as the packets pass through a router. ACLs can be configured at the router to control access to a network or subnet. ACLs filter network traffic by controlling whether routed packets are forwarded or blocked at the router's interfaces. The router examines each packet to determine whether to forward or drop it, based on the conditions specified in the ACL (source address, the destination address, upper-layer protocol, or other information.) ACLs must be defined on a per-protocol basis. In other words, you must define an ACL for every protocol enabled on an interface if you want to control traffic flow for that interface
How ACL Works?
An ACL are a group of statements that defines how packets;
- Enter inbound interfaces
- Relay through the router
- Exit outbound interfaces of the router.
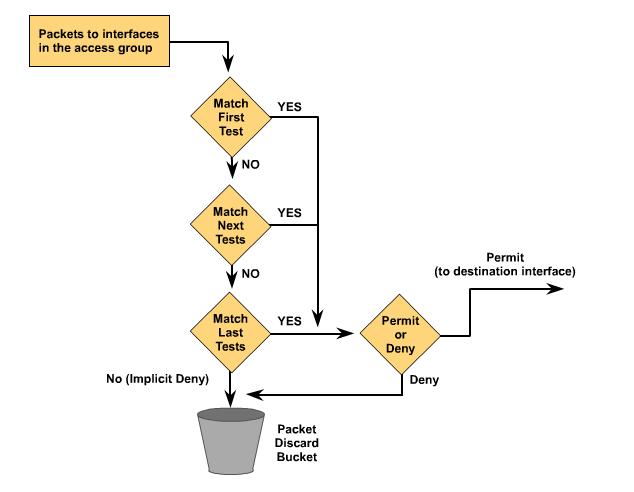
ACL statements operate in sequential, logical order. If a condition match is true, the packet is permitted or denied and the rest of the ACL statements are not checked. If all the ACL statements are unmatched, an implicit "deny any" statement is imposed. This means that even though you will not see the "deny any" as the last line of an ACL, it is there. If the frame entering the router interface matchsthe first test, a packet is denied access to the destination. It is discarded and dropped into the bit bucket, and it is not exposed to any ACL tests that follow. If the packet does not match conditions of the first test, it drops to the next statement in the ACL
Creating ACLs
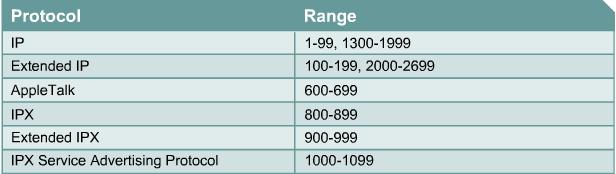
ACL is created in the global configuratin mode. When ACLs are configured on a router, each ACL must have a unique identification number assigned to it. This number identifies the type of access list created and must fall within the specific range of numbers that is valid for that type of list.
After the above commands have been entered the type of ACL (standard/extended) needs to be specified; then the Admin enters the access-list statement using the keyword access-list followed by the proper parameters. The next step is to assigned the ACL to the proper interface. ACL Definition:
STEP 1
<Router>enable
<Router#>configure terminal
<Router config>#access-list <access_list_number>
{permit | deny } <test_condition>
STEP 2 (apply the ACL to the interface by using access group commands)
<Router (config-if)># {protocol} access-group access_list_number
- Use the following rules to create and apply access lists
- There should be one access list per protocol per direction.
- Standard access lists should be applied closest to the destination.
- Extended access lists should be applied closest to the source.
- The inbound or outbound interface should be referenced as if looking at the port from inside the router.
- Statements are processed sequentially from the top of the list to the bottom until a match is found. If no match is found then the packet is denied, and discarded.
- There is an implicit deny any at the end of all access lists. This will not appear in the configuration listing.
- Access list entries should filter in the order from specific to general. Specific hosts should be denied first, and groups or general filters should come last.
- The match condition is examined first. The permit or deny is examined only if the match is true.
- Never work with an access list that is actively applied.
- A text editor should be used to create comments that outline the logic. Then fill in the statements that perform the logic.
- New lines are always added to the end of the access list. A no access-list x command will remove the whole list. It is not possible to selectively add and remove lines with numbered ACLs
- An IP access list will send an ICMP host unreachable message to the sender of the rejected packet and will discard the packet in the bit bucket.
- An access list should be removed carefully. If an access list that is applied to a production interface is removed, some versions of IOS will apply a default deny any to the interface and all traffic will be halted.
- Outbound filters do not affect traffic that originates from the local router.
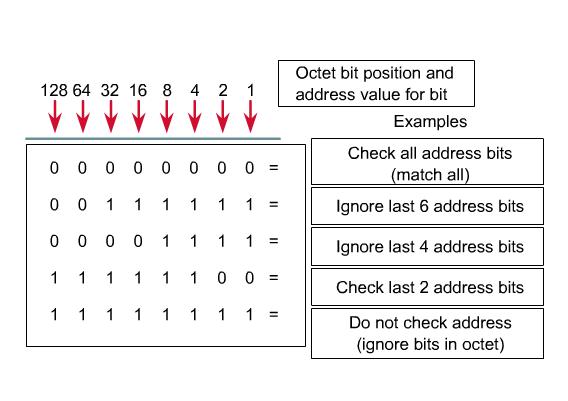
Wildcard Mask
A wildcard mask is a 32-bit quantity that is divided into four octets, with each octet containing 8 bits. A wildcard mask bit 0 means "check the corresponding bit value" and a wildcard mask bit 1 means "do not check (ignore) that corresponding bit value". A wildcard mask is paired with an IP address. The numbers one and zero are used to identify how to treat the corresponding IP address bits. ACLs use wildcard masking to identify a single or multiple addresses for permit or deny tests.