Team Lessig: Code 2.0
From 20803
(→Part IV) |
|||
| (54 intermediate revisions not shown) | |||
| Line 1: | Line 1: | ||
== Code 2.0 by Lawrence Lessig == | == Code 2.0 by Lawrence Lessig == | ||
| - | + | [[Image:Code2.gif|right|]] | |
| - | + | <nowiki>Table of Contents</nowiki> | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
| - | + | ||
*Part I: REGULABILITY | *Part I: REGULABILITY | ||
| Line 37: | Line 29: | ||
*Chapter 19: What Declan Doesn't Get | *Chapter 19: What Declan Doesn't Get | ||
| + | '''FOR FULL TEXT GO TO http://codev2.cc/''' | ||
| + | *CODE 2.0 is the second version of an original book about cyberspace by Lawrence Lessig. | ||
| + | This book is a compilation of the first edition and contributions from the CODE 2.0 Wiki page. | ||
| + | For further information please see [http://www.socialtext.net/codev2/index.cgi THIS LINK] | ||
| + | *For additional information about the author please visit his website [http://www.lessig.org/ LAWRENCE LESSIG] | ||
| - | + | == Part I - From Anonymity to Control == | |
| - | == Part I == | + | |
| - | + | ||
| - | + | ||
'''Chapter 3: Is-Ism: Is the Way It Is the Way It Must Be?''' | '''Chapter 3: Is-Ism: Is the Way It Is the Way It Must Be?''' | ||
| Line 47: | Line 41: | ||
*This chapter explores the idea that most people assume that because the internet is currently not being governmentally regulated, that it will never be, and should never be, regulated. | *This chapter explores the idea that most people assume that because the internet is currently not being governmentally regulated, that it will never be, and should never be, regulated. | ||
*“The original architecture of the internet made regulation very difficult. But that original architecture can change.” | *“The original architecture of the internet made regulation very difficult. But that original architecture can change.” | ||
| + | *However the internet is regulated, or not regulated, today is not the way it HAS to remain. | ||
* Example is Harvard University, where network access is only granted to students and faculty whose identity is known and actions are controlled. | * Example is Harvard University, where network access is only granted to students and faculty whose identity is known and actions are controlled. | ||
*The design of the internet creates an “invisible man” with no physical characteristics. | *The design of the internet creates an “invisible man” with no physical characteristics. | ||
*Therefore, it is difficult to enforce separate, or any, rules among internet users. | *Therefore, it is difficult to enforce separate, or any, rules among internet users. | ||
| + | '''Chapter 4: Architectures of Control''' | ||
| + | *This chapter describes possible changes that could make the internet more regulable. | ||
| + | *However, the main idea is that internet users and commerce, not the government, are demanding regulation. | ||
| + | *Commerce would benefit due to the lack of fraud that would occur with increased regulability. | ||
| + | *To be able to regulate, however, one's identity must be established. | ||
| + | *But authentication of one's identity is difficult to achieve on the "invisible" internet. | ||
| + | *Tracing, however, through IP addresses and Internet Service Providers, is possible. | ||
| + | *This process is simple, and it answers the simple question related to regulation: "Who did what, where?" | ||
| + | *Now, it seems, achieving anonymity on the internet takes effort. | ||
| - | + | '''Chapter 5: Regulating Code''' | |
| + | *The government needs regulate the internet by deploying "technologies of identification" within the architecture of the internet. | ||
| + | *Behavior is regulated by the government by directly regulating the technologies, or codes, that are related to that behavior. | ||
| + | *The government needs to increase and encourage the use of digital identification to ensure security. | ||
| + | *With identification and authentication comes online freedom, but eliminates anonymity. Is the benefit worth the price? | ||
| + | *Overall, architectural control on the Net will increase, but it is important to keep it consistent with public values and interests as well. | ||
| + | |||
| + | |||
| + | |||
| + | == Part II-A Sense of Community== | ||
| + | [[Image:4constraints.png|right|]] [[Image:4constraints-dynamic.png|right|]] | ||
"The aim of this part is to explore this distinctive mode of regulation as a step to understanding more systematically the interaction between technology and policy." | "The aim of this part is to explore this distinctive mode of regulation as a step to understanding more systematically the interaction between technology and policy." | ||
| - | + | Lawrence Lessig | |
'''Chapter 6: Cyberspaces''' | '''Chapter 6: Cyberspaces''' | ||
| Line 65: | Line 79: | ||
*Everytime you use the Internet, you are following a code, a setup, of how the site is controlled or how the community operate | *Everytime you use the Internet, you are following a code, a setup, of how the site is controlled or how the community operate | ||
| - | '''Chapter 7: What Things Regulate''' | + | '''Chapter 7: What Things Regulate''' |
*'''BIG IDEAS''': | *'''BIG IDEAS''': | ||
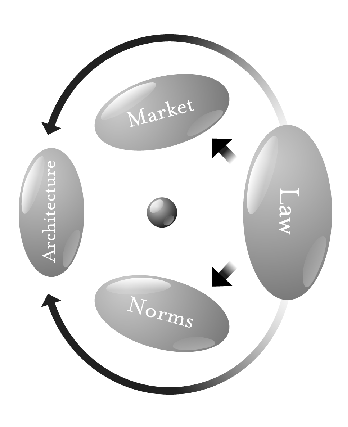
*Lessig explains the four constraints of cyber-spaces which include: Norms, Market, Law, and Architecture | *Lessig explains the four constraints of cyber-spaces which include: Norms, Market, Law, and Architecture | ||
| - | + | *These constraints are meant to aid in understanding how the internet is regulated. Each constraint depends on one another and effects how the cyberspace will function. | |
| - | *These constraints are meant to aid in understanding how the internet is regulated. Each constraint depends on one another and effects how the cyberspace will function. | + | |
| - | + | ||
| - | + | ||
'''Chapter 8: The Limits In Open Code''' | '''Chapter 8: The Limits In Open Code''' | ||
| - | *'''BIG IDEAS''' | + | *'''BIG IDEAS''': |
| - | * | + | *Lessig explains the difference between open and closed codes used for Internet regulation. |
| - | == Part III == | + | *Governments use closed codes because they are not open software. |
| + | *Lessig presents the history of codes in order to alert the reader that the code itself is becoming more and more precise as time goes on. More steps are taken to ensure the code will work successfully. | ||
| + | *Open code can me modified whereas closed code cannot. | ||
| + | |||
| + | |||
| + | == Part III - What does the Internet mean for the aspects of our social lives? == | ||
| + | Lessig not only takes the time to account for the changing aspects of the internet within technology, but references to how this digital medium will affect our lives as humans. What does this change in communication mean for us and our values? After you have read this section, it is in hope that this guide to part three will help you decipher the true meaning in a better way. | ||
| + | |||
| + | It is quite ironic that Lessig's book holds a chapter entitled "Translation." This advanced piece of reading could probably use more of this within it's boundaries, but indeep it does present this topic at least for a little bit. When we consider our liberties, and when Lessig considers our liberties, privacy becomes a medium of ever changing policies and techniques to get on the inside. With the Internet booming, this is more true than ever. With Lessig's presentation of translation being a possibly good solution to solving the new characteristics of our "private lives" it is important for you to consider what indeed Lessig is discussing. Ask yourself these questions... Has your life been affected socially by the new realms within the internet? Do you fully understand what the Internet could do for information that once was sacred and special to only you and a few others, but now is plastered on blogs, websites, and internet databases? Do you understand how your rights are protected? When you have the answers to these consider that Lessig is presenting a way for you to "translate" these new phenomena in your own way. Do not take his consideration or intense studies too literal. His main goal is to challenge the reader to find their own stances involved with their own freedoms and comtemplate if "translation" would help them to live more adjusted within the Internet. | ||
| + | |||
| + | Now as you read and the following liberties are presented within this part, consider these things in lamen terms like I have presented here. Study intently what Lessig presents in detail about each one, but relate them back to yourself as Lessig intended. | ||
| + | |||
| + | Intellectual Property- What is yours on the Internet that you would not want other people to claim? Do you have special material and meaningful information posted up for everyone to just simply take. Are you sure laws exist to protect you? The Internet has created a brand new medium for theft, are you sure your safe? | ||
| + | |||
| + | Privacy- What searchable parts of your life are online. Are you comfortable with the fact that people could be searching through your stuff and intently keyed into the details of your life? Digital media technology has changed the use of many things, from recorders to sources of information, what are you presenting to others about yourself, whether it be values or data? What do you feel can be done to help protect your privacy? | ||
| + | |||
| + | Freedom of Speech- Do you take your liberty of "freedom of speech" more literally when you are on the Internet? Do you even consider the consequences of what you say online? Online freedom of speech is a big area of controversy, are you fueling the fire? | ||
| + | |||
| + | Lessig wants you to approach this part of his book with an open mind, in order to take in his philosophies and apply them to your life. Read his knowledge because it is in depth and relavent to the real understanding of each topic, but as you read use this guide to help develop the ideas within yourself of the subjects discussed. | ||
== Part IV == | == Part IV == | ||
| + | '''Before reading chapter 14 of Lessig's book, consider these notes:''' | ||
| - | An important difference to consider is the idea of Internet vs. Cyberspace. | + | '''An important difference to consider is the idea of Internet vs. Cyberspace'''. |
| - | + | ||
| - | + | - Cyberspace allows control, creativity and freedom. | |
| - | + | - The Internet lacks these qualities and the massive omnipresence of Cyberspace. | |
| - | + | ||
| - | + | ||
| - | + | ||
| - | |||
| - | + | '''Sovereignty and freedom are integral parts of the American persona. Here, Lessig, speaks on the contradiction of this ideal through the internet.''' | |
| - | + | ||
| + | - There are codes upon codes that attempt to "authenticate" the individual entering a website. | ||
| + | |||
| + | - The code is god. It can create, restrict, enable or cripple functions. | ||
| + | |||
| + | - These codes can damage society through its constant control that cannot be found in the real world. | ||
| + | |||
| + | |||
| + | '''Forms of sovereignty''': | ||
| + | |||
| + | '''Merchant Sovereignty''' - The idea to simply take our business somewhere that satifies our needs. If we do not want McDonald's, we can go to Wendy's. They impose rules on us, but we also have a right to choose. | ||
| + | |||
| + | '''Citizen Sovereignty''' - We are like a "stakeholder with a voice". We have a say in the structure and direction of the entity. | ||
The competitive pressure for the attention of the individual is great in cyberspace. | The competitive pressure for the attention of the individual is great in cyberspace. | ||
| - | + | Although there is competition over users, there is great competition between companies to make transition of acquired belongings difficult for its users. | |
| + | The best explanation for chapter 14 lies in a quote from Lessig himself: | ||
| - | '' | + | ''My argument instead is that we must take responsibility for the politics we are building into this architecture, for this architecture is a sovereign governing the community that lives in that space.'' |
| - | + | ||
| - | + | ||
| + | The architecture is sovereign because it can control how its citizens behave and what their options are. | ||
---- | ---- | ||
| + | In chapter 15, keep these notes in mind: | ||
| + | The internet allows for the ownership of a ''dual citizenship''. A person may have a virtual community they belong to, but they are still a member of the real world. This opens the door to bringing certain online activities into one's life and real community. | ||
| + | |||
| + | Possible solutions to the conflict of another theme, jurisdiction control: | ||
| + | |||
| + | '''The No Law Rule''' - All virtual selves should be immune from real world sovereigns. | ||
| + | |||
| + | '''The One Law Rule''' - Only one government dominates by enforcing the law everywhere | ||
| + | |||
| + | '''The Many Laws Rules''' - Have restrictions based on citizenship. For example, Americans would respect the restrictions set forth by their government and Germans would respect the restrictions set in place by their government. They would not be able to violate these laws via cyberspace. | ||
| + | |||
| + | ''With international zoning will come with identification-based regulation. The degree of control that would be possible would be unimaginable.'' | ||
| + | |||
| + | == Part V == | ||
| + | |||
| + | |||
| + | '''After reading PART V consider these:''' | ||
| + | *What is the "Age of the Ostrich?" | ||
| + | *What is it that we have to lose? | ||
'''Chapter 16: The Problems We Face''' | '''Chapter 16: The Problems We Face''' | ||
| Line 149: | Line 207: | ||
*Lawrence Lessig Gives a Speech on You Tube about [http://youtube.com/watch?v=1svJUDq9oho Internet Governance] | *Lawrence Lessig Gives a Speech on You Tube about [http://youtube.com/watch?v=1svJUDq9oho Internet Governance] | ||
| + | |||
| + | |||
== Key Terms == | == Key Terms == | ||
| - | + | * Change from a cyberspace of anarchy to a cyberspace of control. | |
| + | There is concern for the amount and type of regulation in terms of the internet. | ||
| + | Regulation of internet is a far fetched idea because how and who will be able to enforce it | ||
| + | |||
| + | * There are different types of regulation that can be used on internet | ||
| + | A code is how we go about using the internet on a daily basis | ||
| + | |||
| + | * Within the internet there are common rights that are wanted from all | ||
| + | There is a trust that users belongings belong to them only | ||
| + | |||
| + | * Code that we experience everyday affect cyberspace | ||
| + | |||
| + | |||
| + | * Code is the most significant form of law, and it is up to lawyers, policymakers, and especially citizens to decide what values that code embodies | ||
Current revision as of 16:29, 30 April 2008
Contents |
[edit] Code 2.0 by Lawrence Lessig
Table of Contents
- Part I: REGULABILITY
- Chapter 1: Code is Law
- Chapter 2: Four Puzzles from Cyberspace
- Chapter 3: Is-ism
- Chapter 4: Architectures of Control
- Chapter 5: Regulating Code
- Part II: CODE AND OTHER REGULATORS
- Chapter 6: Cyber-spaces
- Chapter 7: What Things Regulate
- Chapter 8: The Limits in Open Code
- Part III: APPLICATIONS
- Chapter 9: Translation
- Chapter 10: Intellectual Property
- Chapter 11: Privacy
- Chapter 12: Free Speech
- Chapter 13: Interlude
- Chapter 14: Sovereignty
- Part IV: RESPONDING
- Chapter 15: The Problems We Face
- Chapter 16: Responses
- Part V: Responses
- Chapter 17: The Problems We Face
- Chapter 18: Responses
- Chapter 19: What Declan Doesn't Get
FOR FULL TEXT GO TO http://codev2.cc/
- CODE 2.0 is the second version of an original book about cyberspace by Lawrence Lessig.
This book is a compilation of the first edition and contributions from the CODE 2.0 Wiki page. For further information please see THIS LINK
- For additional information about the author please visit his website LAWRENCE LESSIG
[edit] Part I - From Anonymity to Control
Chapter 3: Is-Ism: Is the Way It Is the Way It Must Be?
- This chapter explores the idea that most people assume that because the internet is currently not being governmentally regulated, that it will never be, and should never be, regulated.
- “The original architecture of the internet made regulation very difficult. But that original architecture can change.”
- However the internet is regulated, or not regulated, today is not the way it HAS to remain.
- Example is Harvard University, where network access is only granted to students and faculty whose identity is known and actions are controlled.
- The design of the internet creates an “invisible man” with no physical characteristics.
- Therefore, it is difficult to enforce separate, or any, rules among internet users.
Chapter 4: Architectures of Control
- This chapter describes possible changes that could make the internet more regulable.
- However, the main idea is that internet users and commerce, not the government, are demanding regulation.
- Commerce would benefit due to the lack of fraud that would occur with increased regulability.
- To be able to regulate, however, one's identity must be established.
- But authentication of one's identity is difficult to achieve on the "invisible" internet.
- Tracing, however, through IP addresses and Internet Service Providers, is possible.
- This process is simple, and it answers the simple question related to regulation: "Who did what, where?"
- Now, it seems, achieving anonymity on the internet takes effort.
Chapter 5: Regulating Code
- The government needs regulate the internet by deploying "technologies of identification" within the architecture of the internet.
- Behavior is regulated by the government by directly regulating the technologies, or codes, that are related to that behavior.
- The government needs to increase and encourage the use of digital identification to ensure security.
- With identification and authentication comes online freedom, but eliminates anonymity. Is the benefit worth the price?
- Overall, architectural control on the Net will increase, but it is important to keep it consistent with public values and interests as well.
[edit] Part II-A Sense of Community
"The aim of this part is to explore this distinctive mode of regulation as a step to understanding more systematically the interaction between technology and policy." Lawrence Lessig
Chapter 6: Cyberspaces
- BIG IDEAS:
- Cyberspaces give Internet users a easier and different approach to life due to the easy access of things. Ex: Books-Amazon.com
- Lessig provides an easy visual to illustrate his idea of the regulation of cyberspace. He compares regulation to a how prison bars regulate the movement of a prisoner or how stairs regulate the access of the disabled.
- Communities such as America Online and Second Life are communities because the are designed architecturally that way. They are meant to serve the users in a specific way. Each community has rules that are set up as guidelines, to aid in keeping the community organized and easy to use.
- Everytime you use the Internet, you are following a code, a setup, of how the site is controlled or how the community operate
Chapter 7: What Things Regulate
- BIG IDEAS:
- Lessig explains the four constraints of cyber-spaces which include: Norms, Market, Law, and Architecture
- These constraints are meant to aid in understanding how the internet is regulated. Each constraint depends on one another and effects how the cyberspace will function.
Chapter 8: The Limits In Open Code
- BIG IDEAS:
- Lessig explains the difference between open and closed codes used for Internet regulation.
- Governments use closed codes because they are not open software.
- Lessig presents the history of codes in order to alert the reader that the code itself is becoming more and more precise as time goes on. More steps are taken to ensure the code will work successfully.
- Open code can me modified whereas closed code cannot.
[edit] Part III - What does the Internet mean for the aspects of our social lives?
Lessig not only takes the time to account for the changing aspects of the internet within technology, but references to how this digital medium will affect our lives as humans. What does this change in communication mean for us and our values? After you have read this section, it is in hope that this guide to part three will help you decipher the true meaning in a better way.
It is quite ironic that Lessig's book holds a chapter entitled "Translation." This advanced piece of reading could probably use more of this within it's boundaries, but indeep it does present this topic at least for a little bit. When we consider our liberties, and when Lessig considers our liberties, privacy becomes a medium of ever changing policies and techniques to get on the inside. With the Internet booming, this is more true than ever. With Lessig's presentation of translation being a possibly good solution to solving the new characteristics of our "private lives" it is important for you to consider what indeed Lessig is discussing. Ask yourself these questions... Has your life been affected socially by the new realms within the internet? Do you fully understand what the Internet could do for information that once was sacred and special to only you and a few others, but now is plastered on blogs, websites, and internet databases? Do you understand how your rights are protected? When you have the answers to these consider that Lessig is presenting a way for you to "translate" these new phenomena in your own way. Do not take his consideration or intense studies too literal. His main goal is to challenge the reader to find their own stances involved with their own freedoms and comtemplate if "translation" would help them to live more adjusted within the Internet.
Now as you read and the following liberties are presented within this part, consider these things in lamen terms like I have presented here. Study intently what Lessig presents in detail about each one, but relate them back to yourself as Lessig intended.
Intellectual Property- What is yours on the Internet that you would not want other people to claim? Do you have special material and meaningful information posted up for everyone to just simply take. Are you sure laws exist to protect you? The Internet has created a brand new medium for theft, are you sure your safe?
Privacy- What searchable parts of your life are online. Are you comfortable with the fact that people could be searching through your stuff and intently keyed into the details of your life? Digital media technology has changed the use of many things, from recorders to sources of information, what are you presenting to others about yourself, whether it be values or data? What do you feel can be done to help protect your privacy?
Freedom of Speech- Do you take your liberty of "freedom of speech" more literally when you are on the Internet? Do you even consider the consequences of what you say online? Online freedom of speech is a big area of controversy, are you fueling the fire?
Lessig wants you to approach this part of his book with an open mind, in order to take in his philosophies and apply them to your life. Read his knowledge because it is in depth and relavent to the real understanding of each topic, but as you read use this guide to help develop the ideas within yourself of the subjects discussed.
[edit] Part IV
Before reading chapter 14 of Lessig's book, consider these notes:
An important difference to consider is the idea of Internet vs. Cyberspace.
- Cyberspace allows control, creativity and freedom.
- The Internet lacks these qualities and the massive omnipresence of Cyberspace.
Sovereignty and freedom are integral parts of the American persona. Here, Lessig, speaks on the contradiction of this ideal through the internet.
- There are codes upon codes that attempt to "authenticate" the individual entering a website.
- The code is god. It can create, restrict, enable or cripple functions.
- These codes can damage society through its constant control that cannot be found in the real world.
Forms of sovereignty:
Merchant Sovereignty - The idea to simply take our business somewhere that satifies our needs. If we do not want McDonald's, we can go to Wendy's. They impose rules on us, but we also have a right to choose.
Citizen Sovereignty - We are like a "stakeholder with a voice". We have a say in the structure and direction of the entity.
The competitive pressure for the attention of the individual is great in cyberspace.
Although there is competition over users, there is great competition between companies to make transition of acquired belongings difficult for its users.
The best explanation for chapter 14 lies in a quote from Lessig himself:
My argument instead is that we must take responsibility for the politics we are building into this architecture, for this architecture is a sovereign governing the community that lives in that space.
The architecture is sovereign because it can control how its citizens behave and what their options are.
In chapter 15, keep these notes in mind:
The internet allows for the ownership of a dual citizenship. A person may have a virtual community they belong to, but they are still a member of the real world. This opens the door to bringing certain online activities into one's life and real community.
Possible solutions to the conflict of another theme, jurisdiction control:
The No Law Rule - All virtual selves should be immune from real world sovereigns.
The One Law Rule - Only one government dominates by enforcing the law everywhere
The Many Laws Rules - Have restrictions based on citizenship. For example, Americans would respect the restrictions set forth by their government and Germans would respect the restrictions set in place by their government. They would not be able to violate these laws via cyberspace.
With international zoning will come with identification-based regulation. The degree of control that would be possible would be unimaginable.
[edit] Part V
After reading PART V consider these:
- What is the "Age of the Ostrich?"
- What is it that we have to lose?
Chapter 16: The Problems We Face
3 Reasons why American's are disable in properly facing cyberspace issues
- limited courts -
- "It is against this background that we should think about the problems
raised in Parts 3 and 4. In each case, my argument was that we will need to choose the values we want cyberspace to embrace. These questions are not addressed by any clear constitutional text or tradition. In the main, they are questions affecting the codifying part of our tradition, but they are also cases of latent ambiguity. There is no answer to them in the sense of a judgment that seems to have been made and that a court can simply report. An answer must be fixed upon, not found; made, not discovered; chosen, not reported." (Lessig 315)
- limited legislatures -
- "But the problemhere is not with governance in cyberspace.Our problem
is with governance itself. There is no special set of dilemmas that cyberspace will present; there are only the familiar dilemmas of modern governance, but in a new place." (Lessig 320)
- limited thinking - Ask your self these these questions before reading this section and answer them when you're done. -
- "Of course, for the computer scientist code is law. And if code is law, then
obviously the question we should ask is:Who are the lawmakers?Who writes this law that regulates us? What role do we have in defining this regulation? What right do we have to know of the regulation? And how might we intervene to check it?"
Chapter 17: Responses
- For excellent work exploring how cyberspace might advance this general project see:
Beth Simone Noveck, Designing Deliberative Democracy in Cyberspace: The
Role of the Cyber-Lawyer, Boston University Journal of Science and Technology Law 9
Chapter 18: What Declan Doesn't Get
- Check out the website of the guy this chapter is about: Duclan McCullagh
- Lawrence Lessig Gives a Speech on You Tube about Internet Governance
[edit] Key Terms
- Change from a cyberspace of anarchy to a cyberspace of control.
There is concern for the amount and type of regulation in terms of the internet. Regulation of internet is a far fetched idea because how and who will be able to enforce it
- There are different types of regulation that can be used on internet
A code is how we go about using the internet on a daily basis
- Within the internet there are common rights that are wanted from all
There is a trust that users belongings belong to them only
- Code that we experience everyday affect cyberspace
- Code is the most significant form of law, and it is up to lawyers, policymakers, and especially citizens to decide what values that code embodies